[Impressum]
[E-Mail]
Modeling the German
Electronic Health Card (EGK) (3)
The next step is to give an overview of the functionality of the application and to illustrate the interdependencies between the protocols. This is done using activity diagrams. These diagrams are not used for code generation or to generate the formal specification, they are used for illustration only.
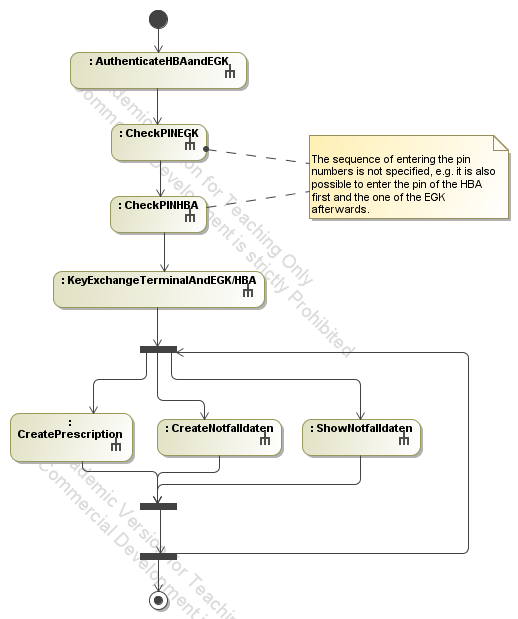
- Protocols executed at a doctor's
office. Participating users and components are the patient, the doctor,
the patient's electronic health card (EGK), the Heilberufsasuweis (HBA)
of the doctor and the PC at the doctor's office (Arzt-PC):
First, the HBA and the EGK exchange their certificates and authenticate
against each other (protocol AuthenticateHBAandEGK). Then, the doctor
and the patient enter their pin numbers which are stored on the
smartcards (HBA and EGK) and validated by the cards (protocols
CheckPINEGK and CheckPINHBA). Afterwards, a session key is generated
and exchanged. This key is made availale to the EGK, the HBA as well as
the doctor's PC (protocol KeyExchangeTerminalAndEGK/HBA). Now, several
protocols implementing the functionality of the application can be
executed. It is now possible to create a prescription, create the
Notfalldaten of the patient (i.e. data that is
needed in case of emergency, e.g. intolerances, diabetes) as well as to
show the Notfalldaten. These protocols can be executed repeatedly
without performing the authentication, entering of the pin numbers and
key exchange again.
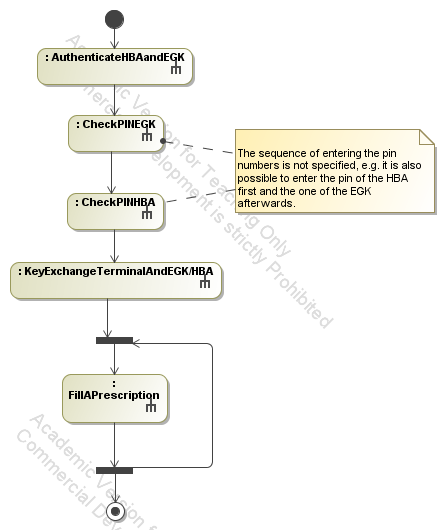
- Protocols executed at a pharmacy. Participating users and components are the patient, the pharmacist,
the patient's electronic health card (EGK), the Heilberufsasuweis (HBA)
of the pharmacist and the PC at the pharmacy (Apotheken-PC):
First, the HBA and the EGK exchange their certificates and authenticate
against each other (protocol AuthenticateHBAandEGK). Then, the doctor
and the patient enter their pin numbers which are stored on the
smartcards (HBA and EGK) and validated by the cards (protocols
CheckPINEGK and CheckPINHBA). Afterwards, a session key is generated
and exchanged. This key is made availale to the EGK, the HBA as well as
the doctor's PC (protocol KeyExchangeTerminalAndEGK/HBA). Now, it is
possible to fill a prescription that is stored on the electronic
health card. This protocol can be executed repeatedly
without performing the authentication, entering of the pin numbers and
key exchange again.
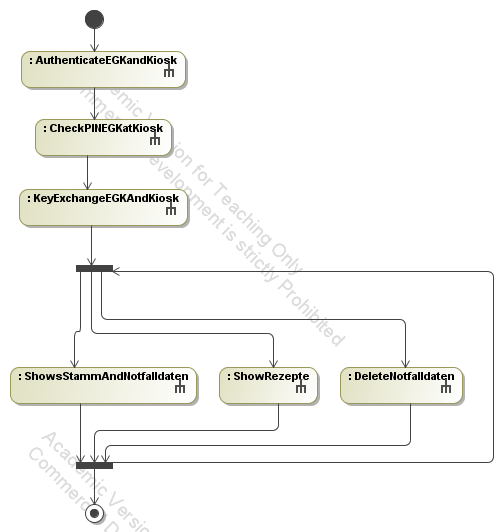
- Protocols executed at a kiosk which is standing in a pharmacy. Participating users and components are the patient,
the patient's electronic health card (EGK) and the Kiosk:
Differently than the doctors PC and the PC in a pharmacy, the kiosk has
its own certificate. In a first step, the kiosk and the EGK exchange
their certificates and authenticate
against each other (protocol AuthenticateEGKandKiosk). Then, the
patient enters his pin number which is stored on and validated by the
EGK (protocol
CheckPINEGKatKiosk). Afterwards, a session key is generated
and exchanged between the kiosk and the EGK (protocol
KeyExchangeEGKAndKiosk). Now, several
protocols implementing the functionality of the application can be
executed. It is now possible to show the Stamm- and Notfalldaten
(i.e. the personal data and data that is
needed in case of emergency), show the prescriptions that are stored on
the card and to delete the Notfalldaten. These protocols can be
executed repeatedly
without performing the authentication, entering of the pin numbers and
key exchange again.
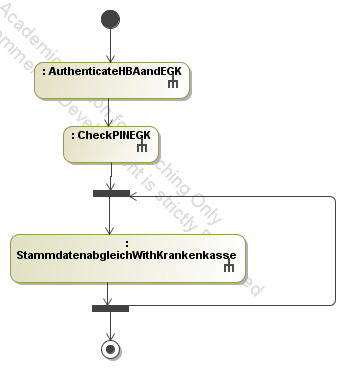
- Protocols executed to compare the
personal data of a patient (stored on the health card) with the data
stored at the health insurance company. Participating users and
components are the patient, the doctor (who initiates the protocol),
the patient's electronic health card (EGK),
the PC at the doctor's office (Arzt-PC) and a service at the health
insurance company which provides the comparison of the data:
First, the HBA and the EGK exchange their certificates and authenticate
against each other (protocol AuthenticateHBAandEGK). Then, the
patient enters his pin number which is stored on and validated by the
EGK (protocol
CheckPINEGK). Afterwards, it is possible to do the comparison between
the personal data stored on the health card and the one stored by the
health insurance company (protocol StammdatenabgleichWithKrankenkasse).
Back, continue to Activity diagrams showing the protocols of the application