[Impressum]
[E-Mail]
Modeling E-Ticket (2)
The data types and messages are described with UML class
diagrams and the communication structure and attacker capabilities with
an UML deployment diagram.
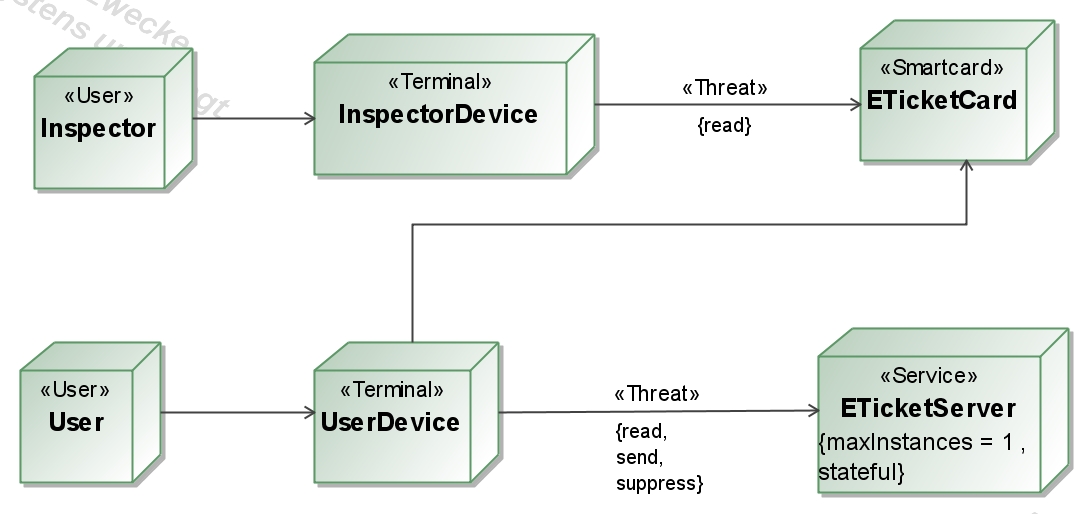
- The
attacker capabilities are described in the deployment diagram by the
stereotype <<Threat>>. Our attacker model support a full Dolev-Yao attacker who can read, send and suppress messages (see UserDevice <-> ETicketServer) but also an attacker who support only a subset of the abilities of a Dolev-Yao attacker (see InspectorDevice <-> ETicketCard). The
User models a human that interacts with a terminal, and we are not
really interested in "attacks'' against a real person.
- Classes with the stereotype <<Service>>, <<Terminal>>, <<Smartcard>> or <<User>>
describe components. This components have some attributes and use
messages to interact with each other. Messages are classes that are
derived from a class with the stereotype <<Message>>. The security property for this application is modelled in the class diagram as an OCL constraint.

Message classes divided by protocols

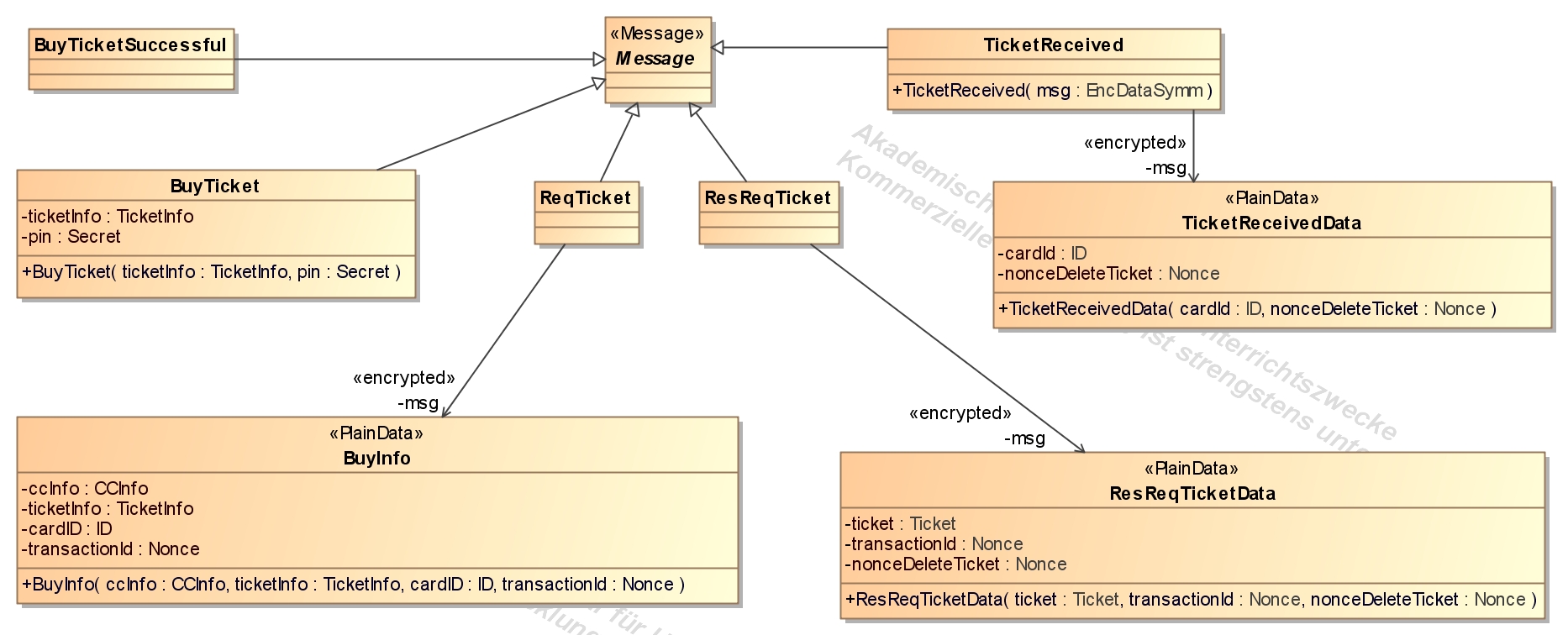
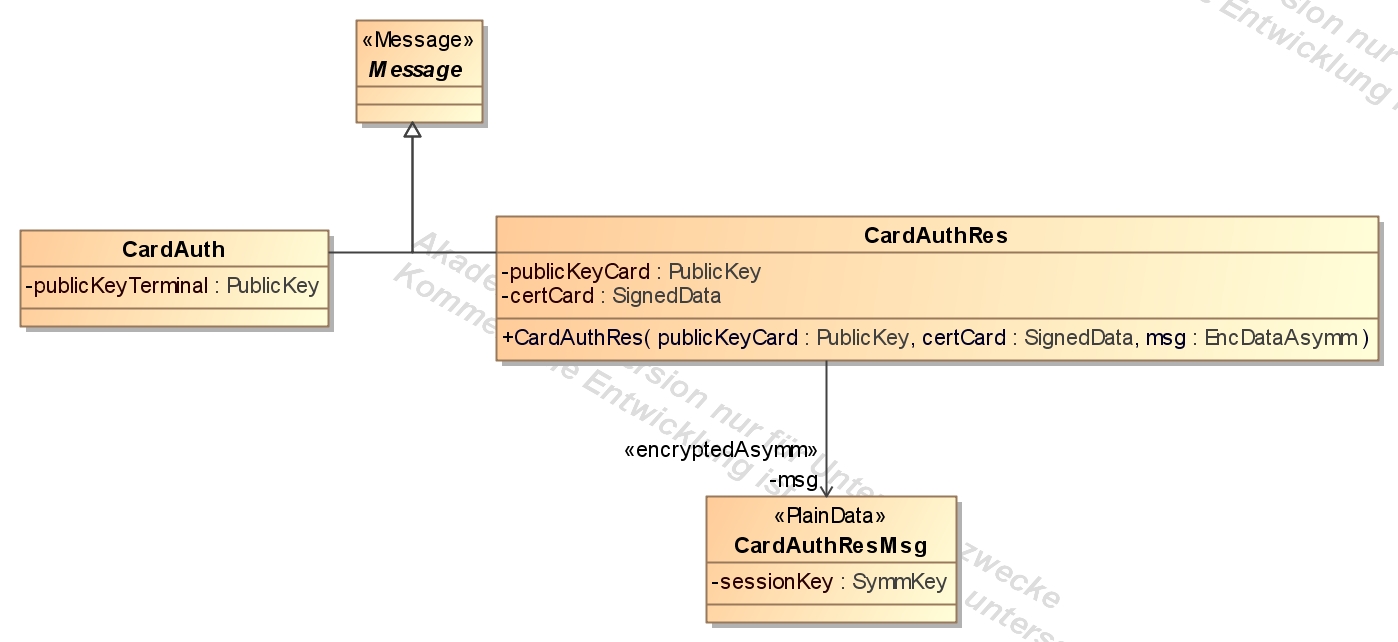
- cardAuthentication and stampTicket:
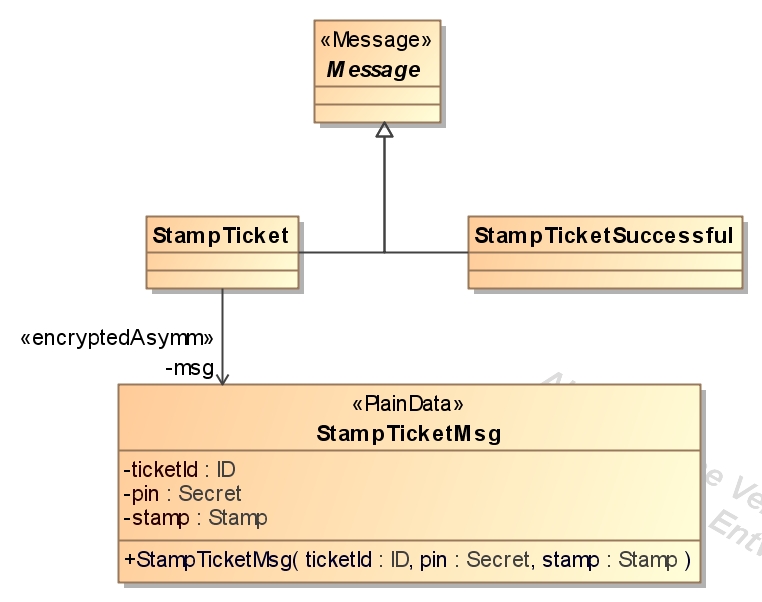
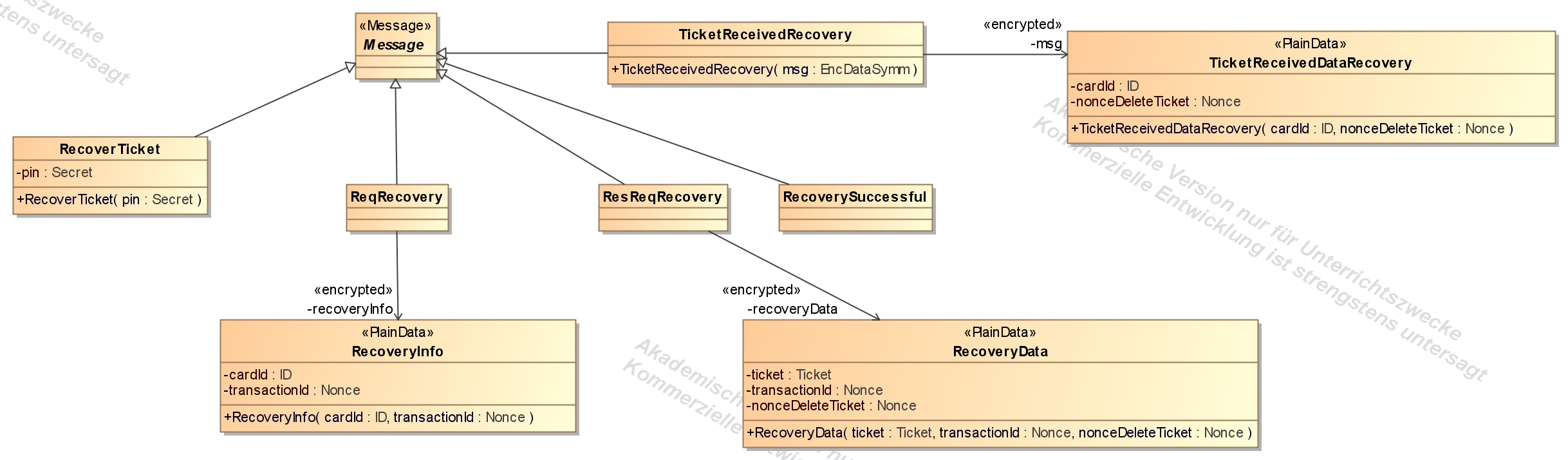
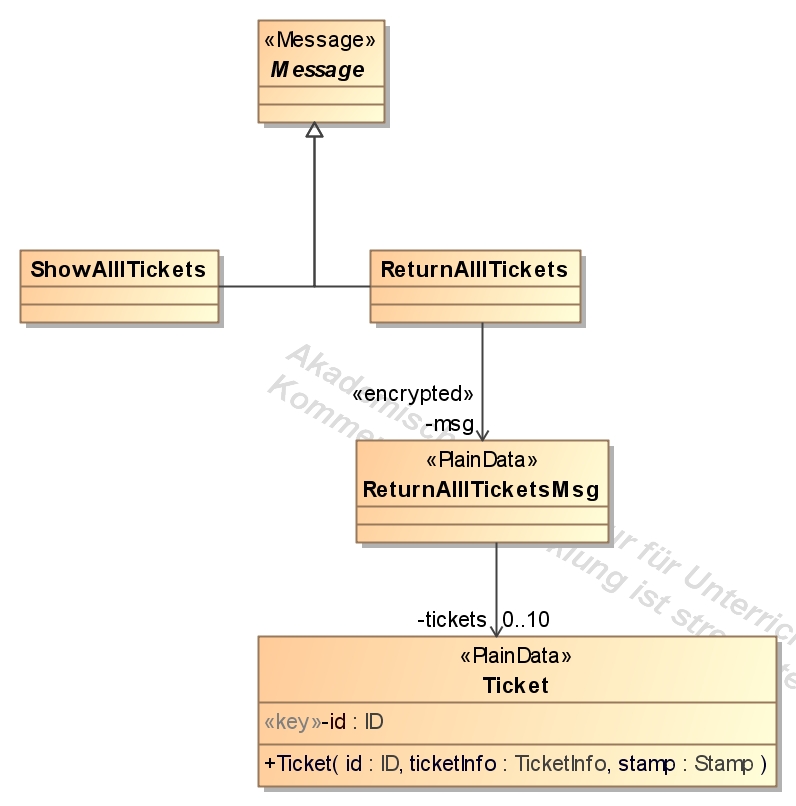
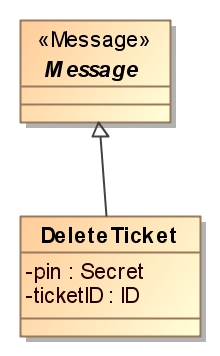
- return all tickets by inspector, return all tickets by card owner and delete ticket:

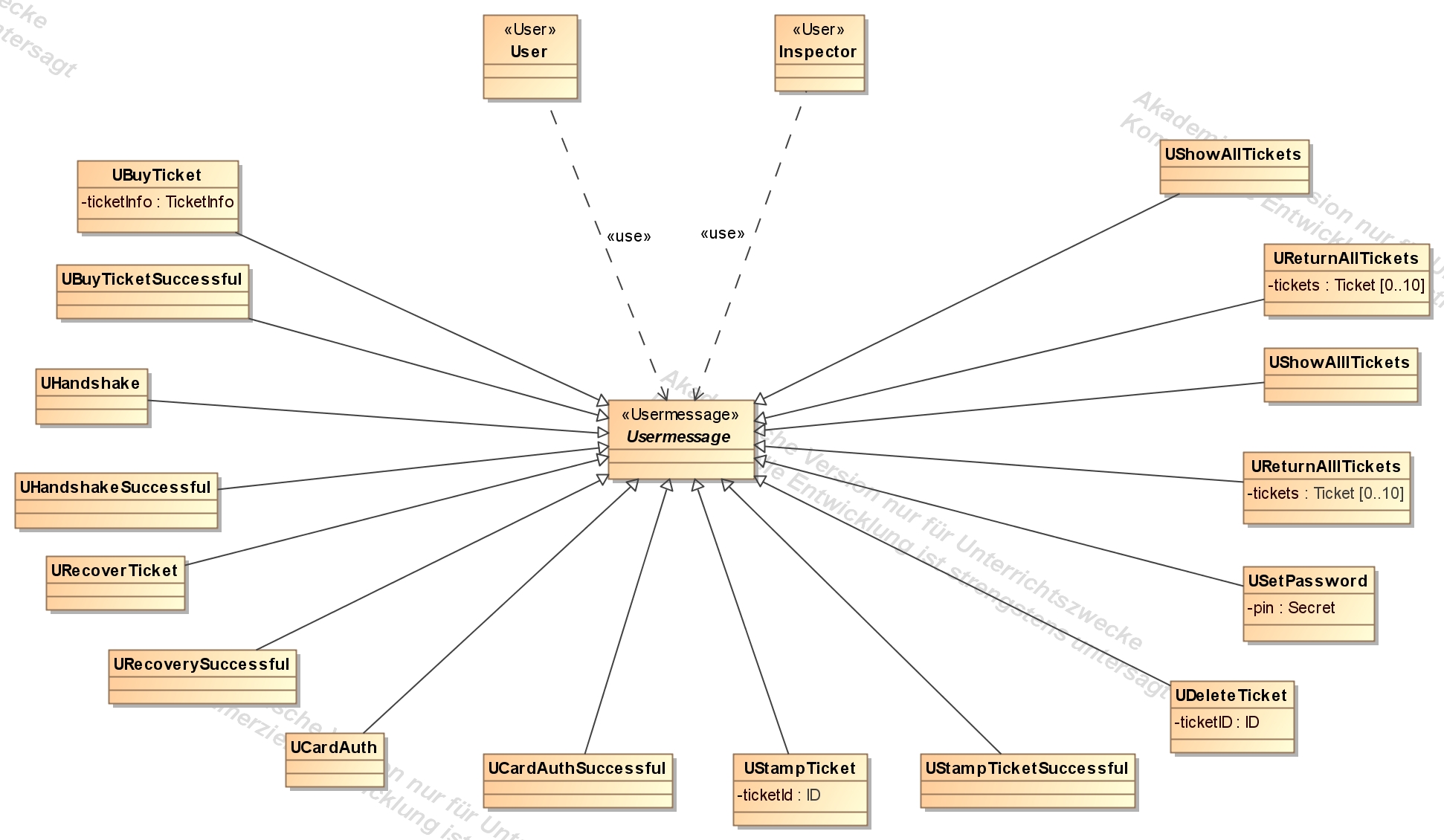
All user messages
Back, Next Step: Detailed model with activity diagrams









