[Impressum]
[E-Mail]
Modeling Debitcard (2)
The
next step is to describe the data types and messages with UML class
diagrams and the communication structure and attacker capabilities with
an UML deployment diagram.
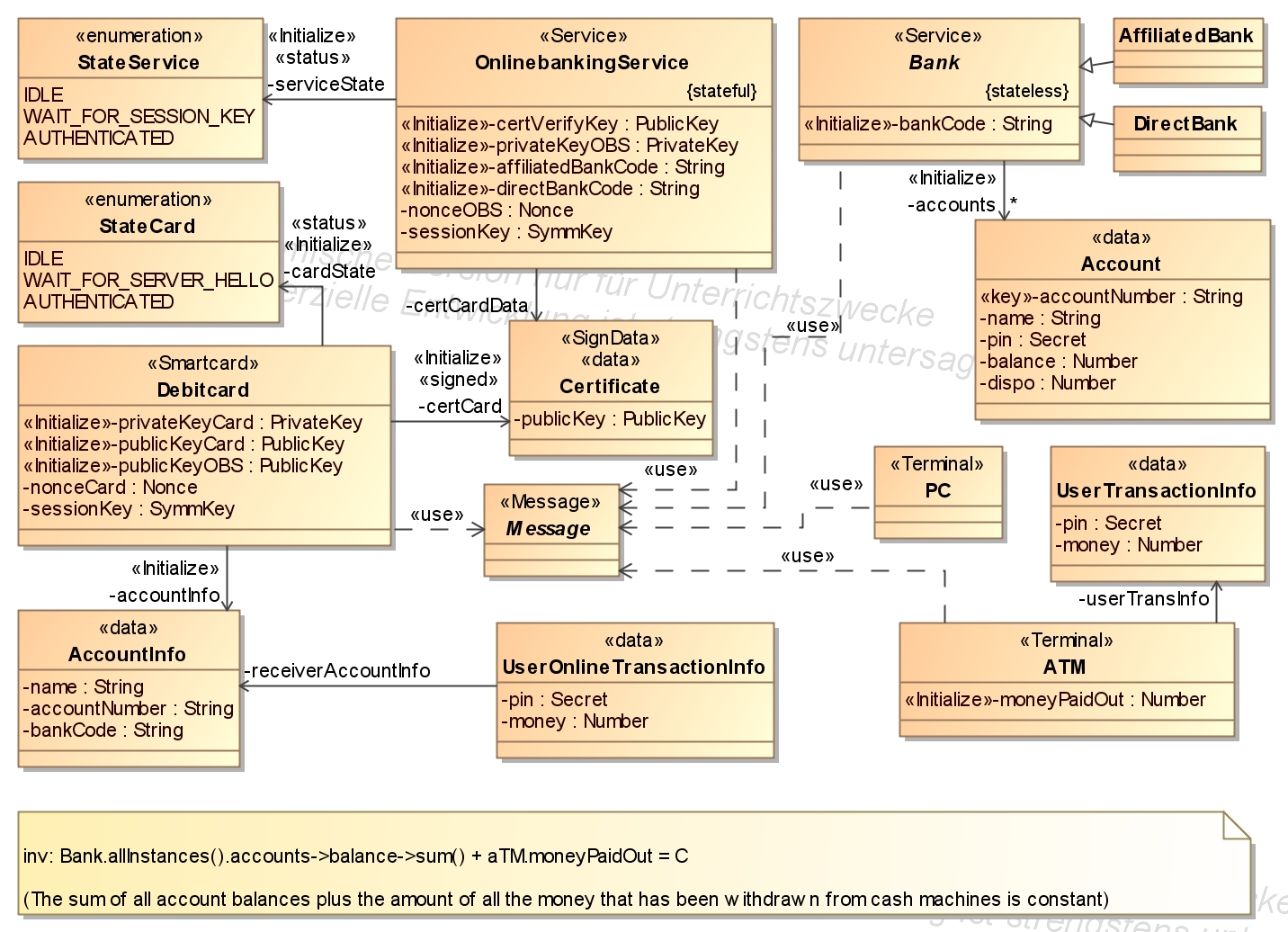
- Classes with the stereotype <<Service>>, <<Terminal>>, <<Smartcard>> or <<User>>
describe components. This components have some attributes and use
messages to interact with each other. Components can be subclasses from
an abstract class, e.g. AffiliatedBank and DirectBank are subclasses from Bank. The security property (The sum of all account balances plus the amount of all the money that has been withdrawn from cash machines is constant)
we proved for this application is modelled in the class diagram as an
OCL constraint. The banks are defined as stateless services that
contains a list of accounts. OnlinebankingService
is a public interface that is invoked if an account owner makes a
transfer from home. Because smart cards does not support TLS a
self-defined protocol between the service (OnlinebankingService) and a smart card (Debitcard) a is used. This protocol base on session dependent states and keys. To simplify the modeling the service (OnlinebankingService) is defined as stateful that means that every invoker get a new instance of OnlinebankingService.
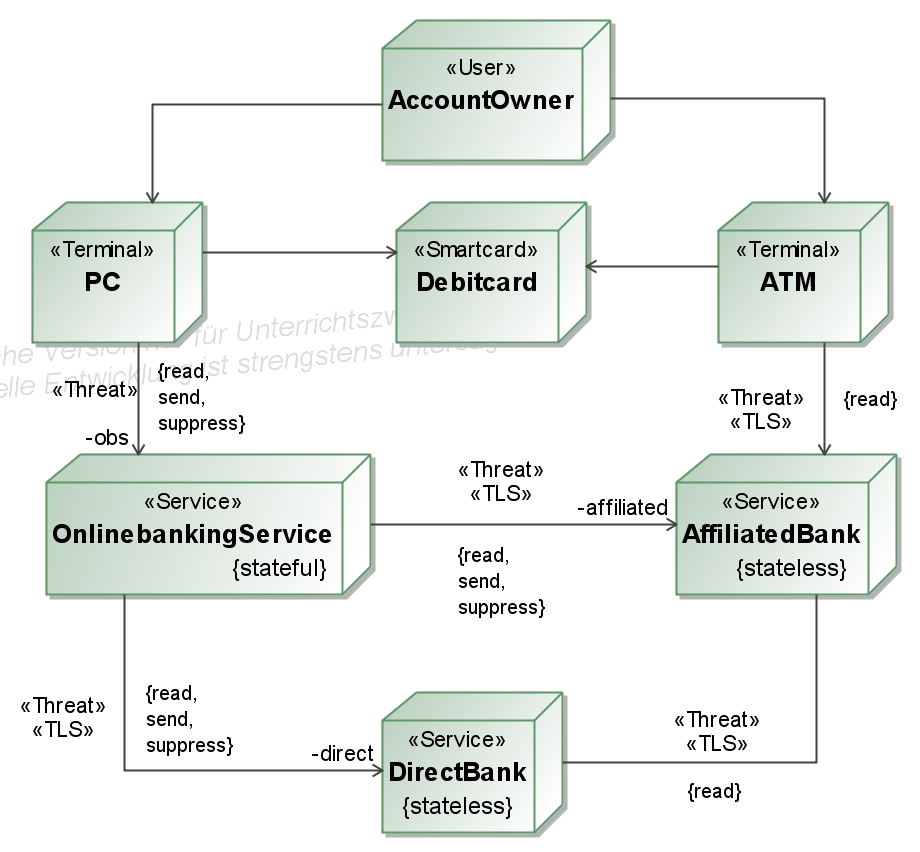
- The attacker capabilities are described in the deployment diagram by the stereotype <<Threat>>. Our
attacker model support a full Dolev-Yao attacker who is able to read,
send, and suppress messages on the fly, but also an attacker who can
also have only a subset of these abilities. The stereotype <<TLS>>
describes that Transport Layer Security with mutual authentication will
be applied. This will influence the attacker abilities . <<User>> models a human that interacts with a <<Terminal>>, and we are not really interested in "attacks'' on the communication area between a user and a terminal.
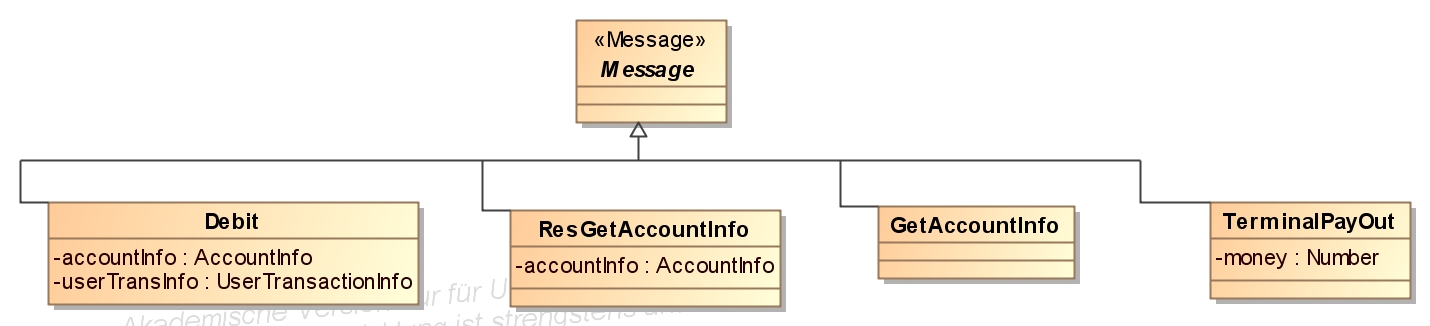
- Messages that are exchanged between components (exclude the user messages) are defined as classes that derive from the class Message.
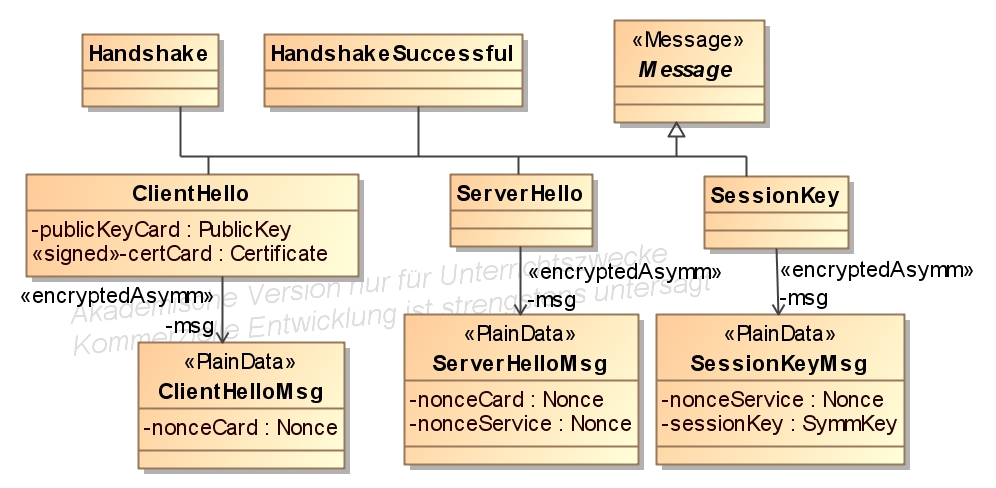
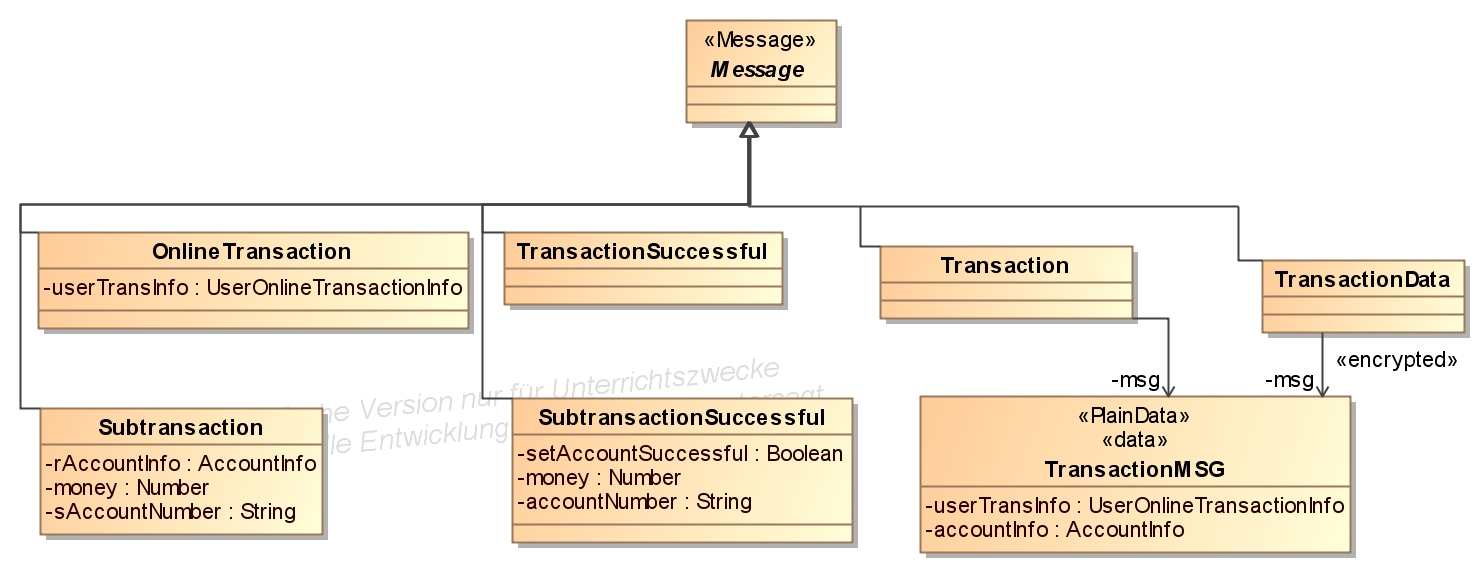
- Messages between an user and a terminal are derived from a class with the stereotype Usermessage.
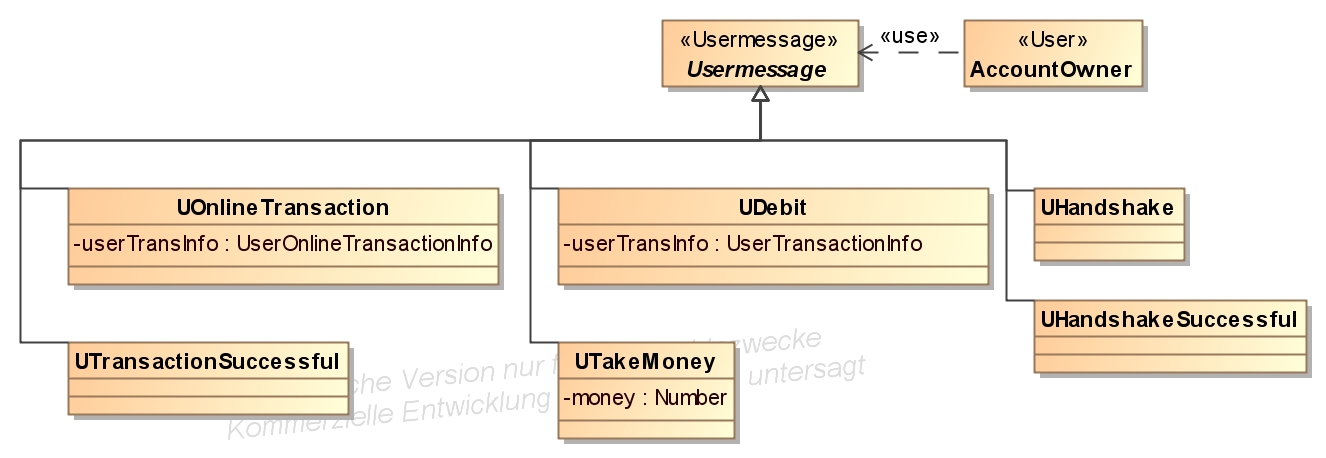
Back, Next Step: Detailed model with activity diagrams




